The web server has to be in the domain.
If the web server is separated by a DMZ firewall, the following ports to the domain controllers need to be opened:
• 88 TCP/UDP – Kerberos
• 389 TCP/UDP – LDAP
• 636 TCP – LDAP SSL
• 135 TCP – RPC Endpoint Mapper
• 53 TCP/UDP – DNS
• 123 UDP – NTP
• 445 TCP – SMB
• 3268 TCP – LDAP Global Catalog
• 3269 TCP – LDAP Global Catalog SSL
• 49152 – 65535/TCP – RPC dynamic high ports (LSA, SAM, Netlogon, FRS)
If the default dynamic high port range is to be restricted, the following registry values must be configured on all domain controllers. The domain controllers must then be restarted.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters
DCTcpipPort (REG_DWORD)
Value data: 49256 (decimal)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
TCP/IP port (REG_DWORD)
Value data: 49257 (decimal)
Refer to:
https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/config-firewall-for-ad-domains-and-trusts
https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/restrict-ad-rpc-traffic-to-specific-port
For the following steps, we assume that BMD Web is already fully set up and operating smoothly.
Refer to:
BMD Web: Setting up web applications
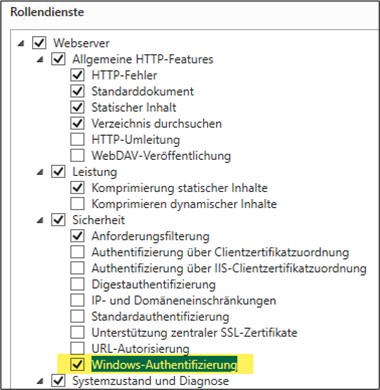
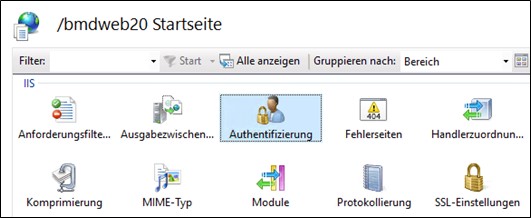
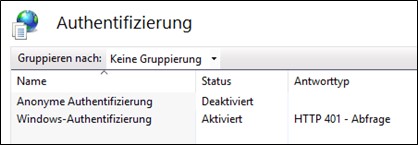
Now, windows authentication needs to be installed on the IIS.
Via PowerShell:
| PowerShell |
| Add-WindowsFeature Web-Windows-Auth |
Via Server Manager:
Manage → Add Roles and Features → Web Server (IIS) → Role Services → Security → Windows Authentication
- Internet Explorer and Edge should now work out of the box.
- For Firefox, you have to search for “network.automatic” via about:config.
Either add the respective URL to “network.automatic-ntlm-auth.trusted-uris” or set “network.automatic-ntlm-auth.allow-non-fqdn” to true and do not fill in “network.automatic-ntlm-auth.trusted-uris”. - Chrome (and browsers that are based on it like Opera and Vivaldi) access the Internet Explorer settings.
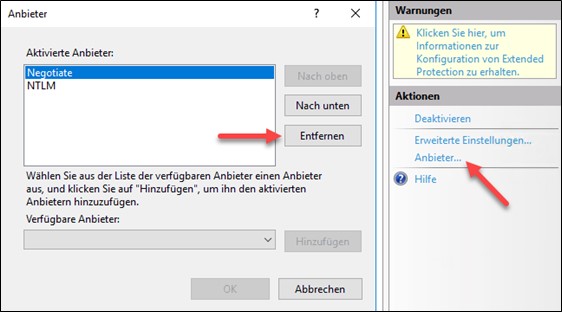
Should it still not work in Chrome, you may have to remove the “Negotiate” provider.
- In private or incognito mode, Windows authentication via NTLM/Kerberos does not work by default.
- If the client from which the website is accessed is not in the domain, a query window opens where you have to enter the user and the password.
After entering the domain credentials, you are permitted access.
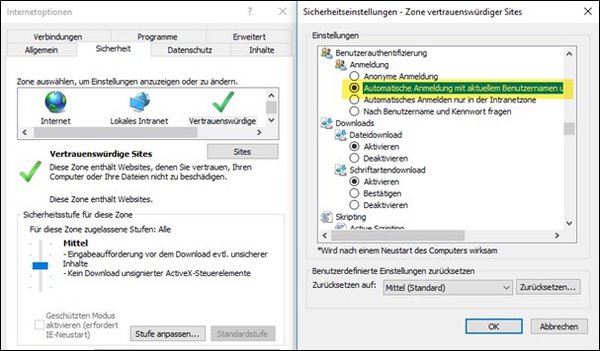
If the system does not assign the URL to BMD Web correctly, please proceed as follows:
- Add the BMD Web URL to the “Trusted sites” in Internet Explorer.
- Set user authentication to “Automatic logon with current username and password”.